Even if NIS2 doesn’t apply to you directly, customer and partner demands can still bring their obligations to your doorstep.
ComplyCloud helps software companies stay ahead - proving compliance without slowing growth.
One solution to support you at every step of NIS2
A mix of legal support and a compliance platform help you become and stay NIS2 compliant.





Your benefits of a complete NIS2 solution
Let us interpret the NIS2 requirements for you
ComplyCloud has developed a practical guide based on the minimum requirements of the NIS2 Directive. All requirements are translated into concrete tasks and documents that you can work with directly in the platform.
Stay compliant with sector-specific rules, backed by legal support
Our legal team ensures that you not only meet the general NIS2 requirements but also comply with any additional rules relevant to your specific industry.
Make NIS2 compliance your competitive edge
Prove to customers and partners that you take security seriously - with legal documentation to back it up.
Some of the NIS2-affected sectors we help


For utility providers, NIS2 isn’t optional - it’s essential. But meeting the requirements doesn’t have to mean complexity or high consulting costs.
ComplyCloud gives utility companies a structured, legally backed platform that simplifies documentation, reduces workload, and supports internal ownership of compliance.


Energy companies are at the core of Europe’s critical infrastructure - and NIS2 sets high expectations for security and documentation.
ComplyCloud helps energy providers like Nord Energi turn those complex requirements into a structured, actionable process backed by legal expertise.


All the services and tools you need to tackle NIS2
NIS2 support by lawyers
Whether you need NIS2 legal support, full compliance outsourcing, or something in between, our flexible Managed Services solution is the right fit for you.

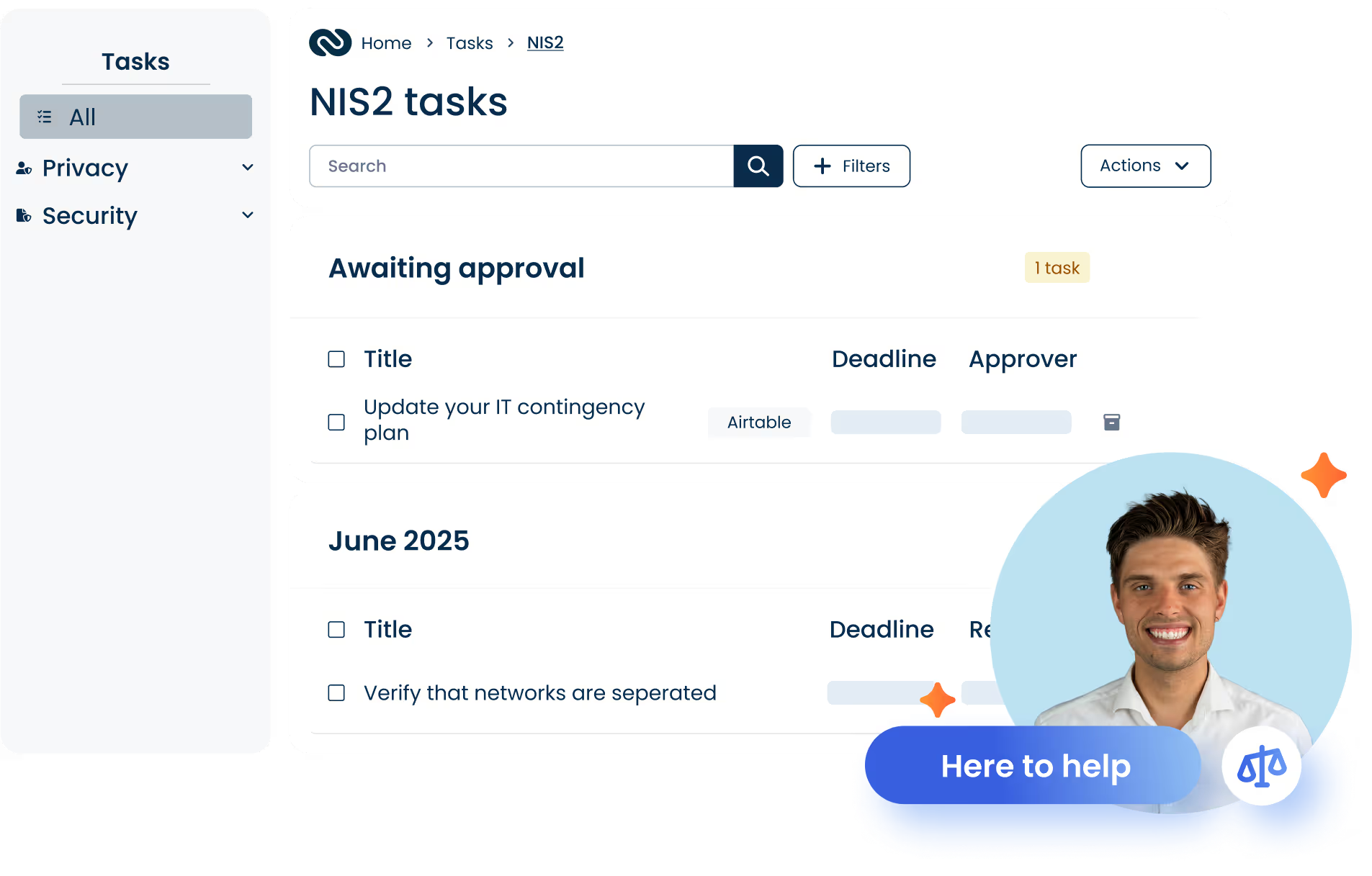
Turn NIS2 compliance into a structured, ongoing process
ComplyCloud’s Annual Cycle of Work transforms NIS2 requirements into a concrete, actionable plan - so you always know who needs to do what, and when.

Receive automatic task reminders that guide you through the requirements step by step.

Assign tasks across the organization and ensure nothing slips through the cracks.

Track progress and plan ahead with a clear overview of what’s completed - and what’s still pending.
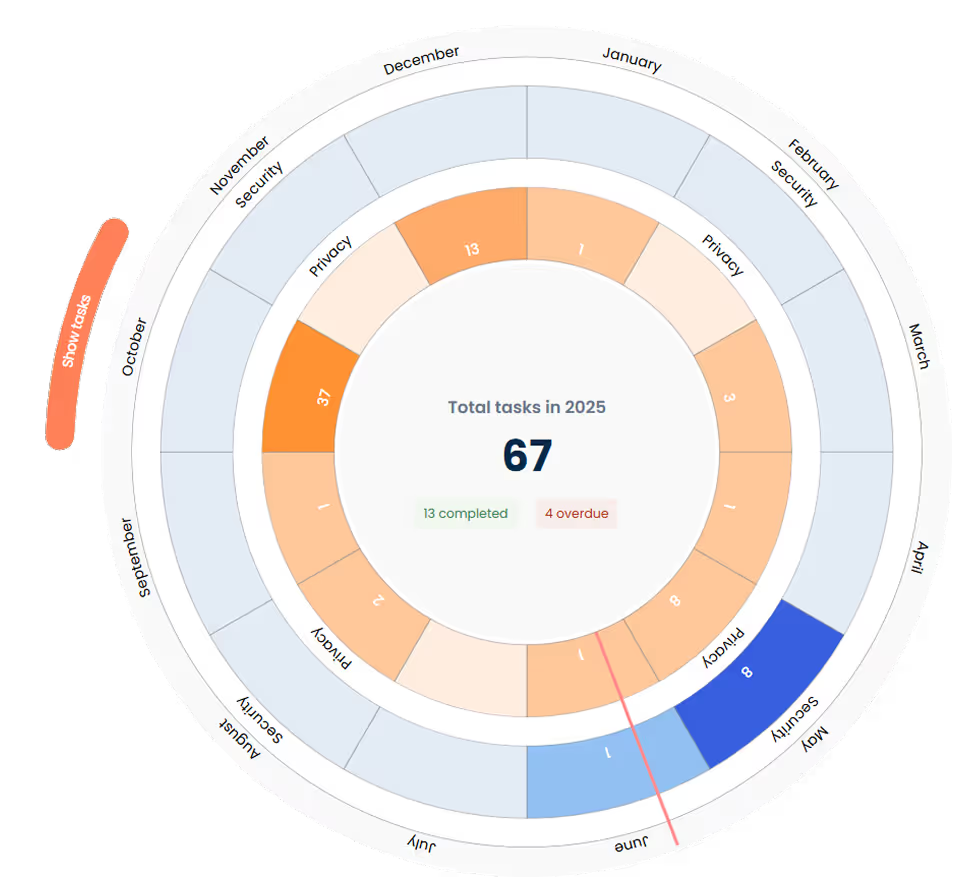
One view of systems and assets - one place to manage risks
By centralizing critical systems, assets, and vulnerabilities, you can detect threats faster, prioritize what matters, and risk assess with confidence.

Make quick high-level assessments or drill into critical assets for deeper risk assessments.

Document security measures, assign approvers, and monitor changes to maintain control.

See how your risk landscape improves over time and export reports to show progress.
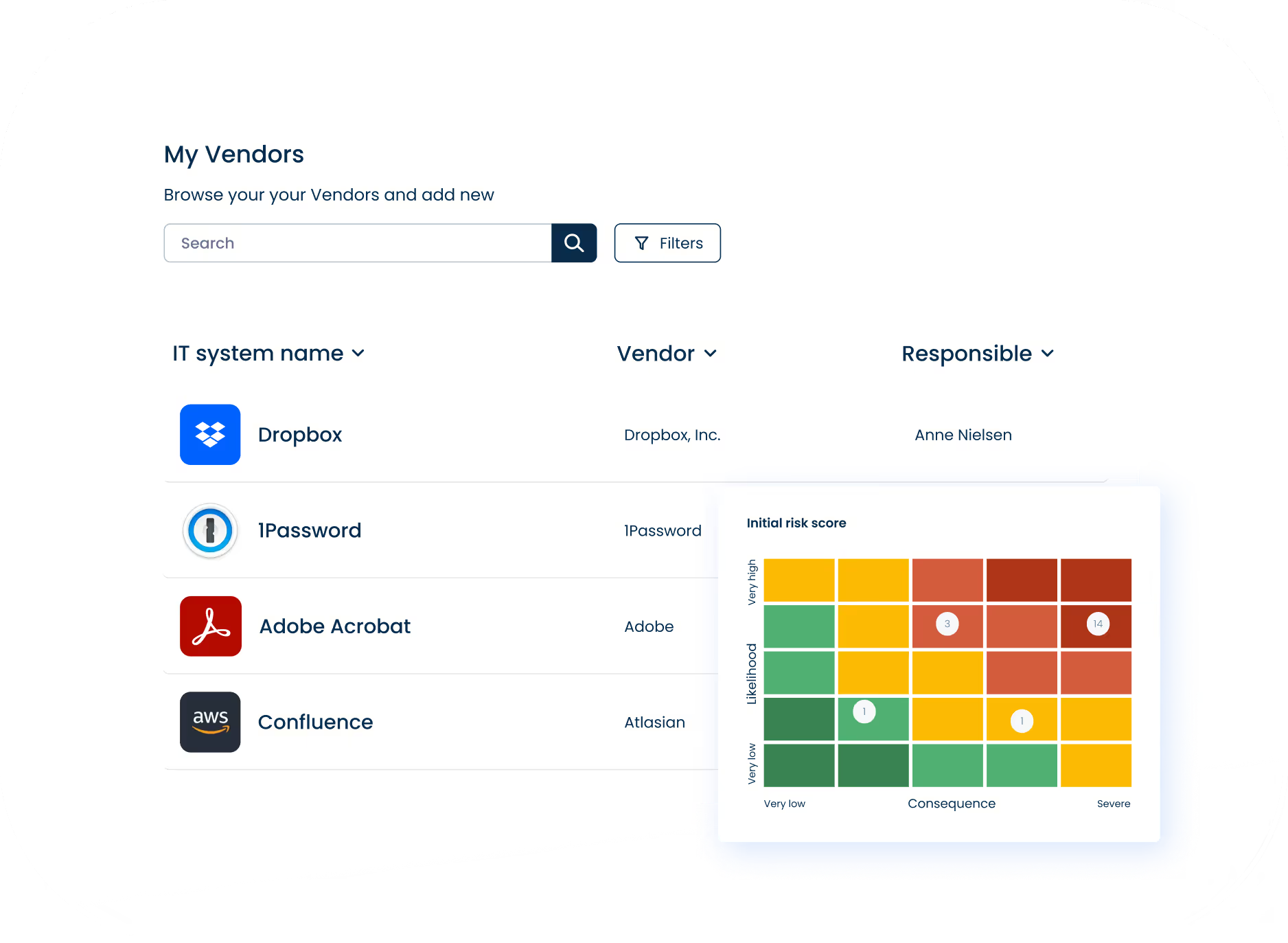
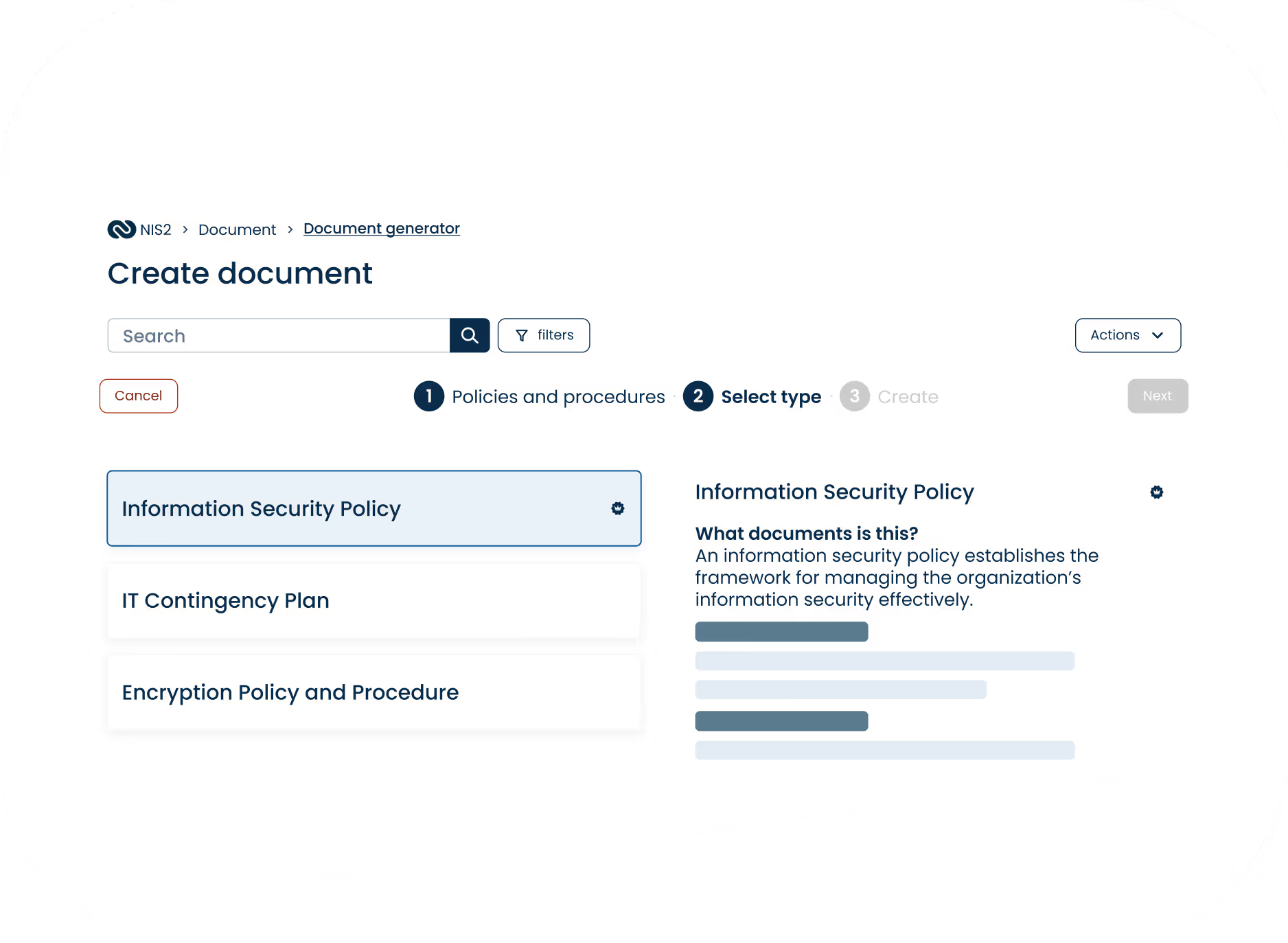
Audit-ready NIS2 documentation
Access all NIS2 documentation from one place including version history and built-in compliance guidance.

Create compliant NIS2 documentation through easy, structured questionnaires.

Keep documents up to date with reminders, and automatically track every change.

Build a Trust Center to demonstrate your NIS2 commitment with evidence.
NIS2 e-learning that sticks
ComplyHero makes NIS2 awareness easy and effective with engaging e-learning modules that are based on your organization’s real risks and responsibilities.

Bite-sized modules reflecting real-world risks so employees remember the knowledge that matters.

Trackable progress to prove awareness and compliance so you can document training efforts and stay audit-ready.

Always up to date with NIS2 and legal requirements so your team is never behind on their obligations.

Ready to take control of NIS2?
Book a live demoDive into our most popular NIS2 content

Compliance Guide for Supply Chain Security within NIS2

NIS2 for Board Members: Understanding Your Obligations and How to Comply

Your NIS2 Playbook: How to Get Compliant Step-By-Step
Frequently asked questions
The NIS1 directive was introduced as the EU’s initial cybersecurity legislation to enhance the ability of network and information systems to withstand cyber risks. However, the COVID-19 pandemic has expanded the range of threats, necessitating the development of new measures.
The European Commission recognized certain shortcomings in the existing NIS1, including:
- Inconsistent resilience levels across Member States and sectors
- A lack of shared understanding regarding threats
- Inadequate joint crisis response capabilities
- Insufficient cyber resilience among EU businesses
Consequently, in December 2020, the Commission put forth new regulations aimed at reinforcing cyber resilience within the EU, which were subsequently adopted in November 2022.
The NIS2 is a directive which means that it will have to be implemented with national legislation. The member states in the EU must do so before 18 October 2024.
The NIS2 directive covers entities from the following sectors:
Essential sectors:
- Energy (electricity, oil, gas, district heating and cooling, and hydrogen).
- Transport (air, rail, water and road)
- Healthcare
- Water supply (drinking water, wastewater).
- Digital infrastructure (telecom, DNS, TLD, cloud service, data centres, trust service providers).
- Finance (banking, financial market infrastructure)
- Public administration
- Space
Important sectors:
- Digital providers (online markets, search engines, social networks)
- Postal services
- Waste management
- Foods
- Manufacturing (medical devices, electronics, machinery, transport equipment)
- Chemicals (production and distrubition)
- Research
While both essential and important sectors are required to adhere to the same security measures, there is a difference in the level of supervision. Entities classified as “essential” are subject to proactive supervision, meaning they are monitored regularly to ensure compliance. On the other hand, “important” entities are monitored only in response to reported incidents of non-compliance.
This differentiation aims to prioritize the continuous operation and resilience of critical services while still ensuring that all entities maintain the necessary security measures to protect against cyber threats.
The NIS2 establishes a comprehensive framework for supervisory and enforcement activities across Member States. Competent authorities are responsible for overseeing essential and important entities’ compliance with the regulations. Supervisory measures include audits, checks, information requests, and access to documents.
The directive introduces a consistent framework for sanctions, including binding instructions, implementation of security audit recommendations, alignment with NIS requirements, and administrative fines. Administrative fines vary based on entity classification, with essential entities facing fines up to €10,000,000 or 2% of annual turnover, and important entities facing fines up to €7,000,000 or 1.4% of annual turnover. Supervisory authorities must consider the nature and severity of the breach and any damages or losses incurred when exercising enforcement powers.
Opposite to the GDPR, the NIS2 also holds natural persons in senior management positions within covered entities accountable.
The NIS2 focuses on improving cyber risk management through clear responsibilities, effective planning, and enhanced cooperation within the EU.
To achieve this, NIS2 mandates Member States to designate national authorities responsible for cyber crisis management. It also introduces the requirement for national large-scale cybersecurity incident and crisis response plans. Additionally, NIS2 establishes the European cyber crisis liaison organization network (EU-CYCLONe). This network plays a vital role in the EU’s cyber crisis management framework, facilitating coordinated responses to significant cybersecurity incidents and crises. The combination of designated authorities, national response plans, and the EU-CYCLONe network ensures a more coordinated and efficient approach to managing large-scale cybersecurity incidents and crises across the European Union.
NIS2 will strengthen and streamline cybersecurity requirements for covered entities by requiring all companies to address a core set of 10 minimum requirements in their cybersecurity risk management policies.
These elements include incident handling, supply chain security, vulnerability handling and disclosure, and the use of cryptography. The NIS2 also includes a multiple-stage approach to incident reporting, which strikes a balance between swift reporting to prevent the spread of incidents and in-depth reporting to draw valuable lessons learned.
Affected companies have 24 hours to submit an early warning, 72 hours to submit an incident notification, and one month to submit a final report. This will help to reduce the additional burden for companies operating in multiple member states and ensure that all companies are addressing the necessary cybersecurity requirements.
Automating NIS2 compliance can help streamline and simplify the process for covered entities. ComplyCloud are currently developing a powerful tool to do exactly this.
Below, we have listed areas where we see a major potential in helping you automating and streamlining your NIS2 compliance:
- Annual wheel of work: An annual wheel of work regularly giving you tasks will make sure you don’t miss anything in your ongoing work and give you peace of mind.
- Risk assessment and management: Automated methods to conduct regular risk assessments, identify vulnerabilities, and prioritize mitigation efforts.
- Incident management: A simple and intuitive incident management system can help you getting managing incidents in a smooth and compliant wat.
- Documentation: Dynamic questionnaires can make you capable of creating any necessary document much faster and with a higher quality than if you had to create them from scratch.
- Employee training and awareness: Carrying out awareness training ensuring that your employees are knowledgeable about their roles and responsibilities under NIS2 will be key to strengthen your organization’s security against cyber-attacks.
- Gap-analyses: Gap-analyses will guide you through the requirements and make you aware of any gaps you might have.
- Vendor management: A system for vendor management will help you comply with the requirements to supply chain security.
