Follow the trusted path to DORA compliance
Take your financial institution through DORA’s requirements - with audit-ready evidence and expert legal support.

Your benefits of our DORA offering
Stay on top of your DORA tasks
The ComplyCloud platform breaks down DORA controls into manageable to-dos you can assign, track, and document - so daily compliance work becomes part of your routine.
Reduce ICT risks
Map your IT systems and vendors, assess risks with built-in guidance, and audit your ICT providers to lower risks in your supply chain.
Save time with onboarding from legal experts
Our legal team help you get started in the platform and offers ongoing support to ensure you and your team are set up for success.
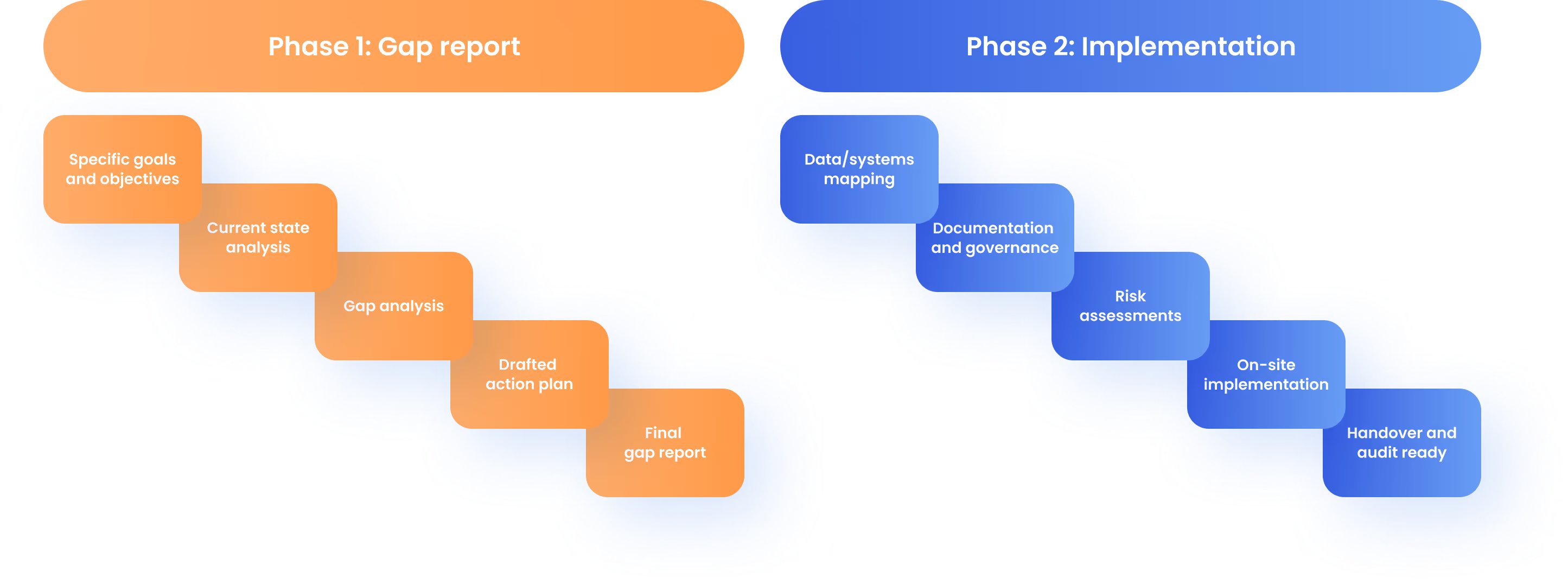
Do you want us to handle the entire DORA project for you?
If you’re short on time or internal resources, our legal team can handle the entire DORA implementation project for you. With our end-to-end Legal Services we help you through the DORA legislation in two phases:
All the features you need to work on DORA
Work on ISO controls mapped to DORA
DORA requirements are translated into ISO 27001 controls and tasks so you can focus on getting things done.
Each control is broken into tasks with owners and due dates to ensure accountability.
ISO-aligned structure supports easier compliance across multiple standards.
Exportable evidence of your actions prepares you for audit and lets you keep track of the progress.

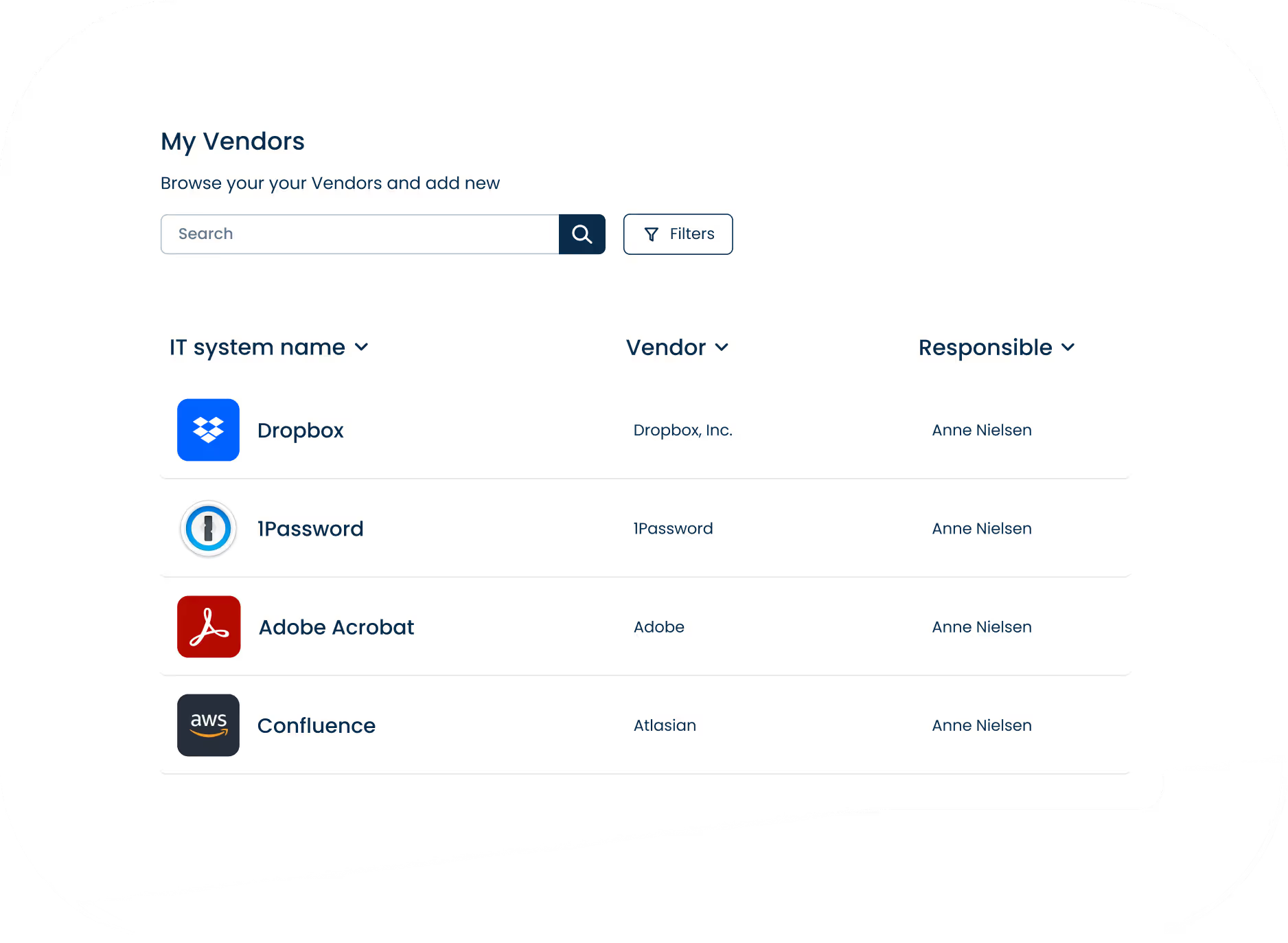
Manage ICT-third parties
Map your entire ICT environment and get the full overview of your IT landscape.
Link vendors to IT systems, sub-processors, and business processes, and gain control of your supply chain.
Access a fully guided audit experience of your ICT providers with recommendations on what to do next.
Assign departments and owners to systems and ensure accountability across the organization.
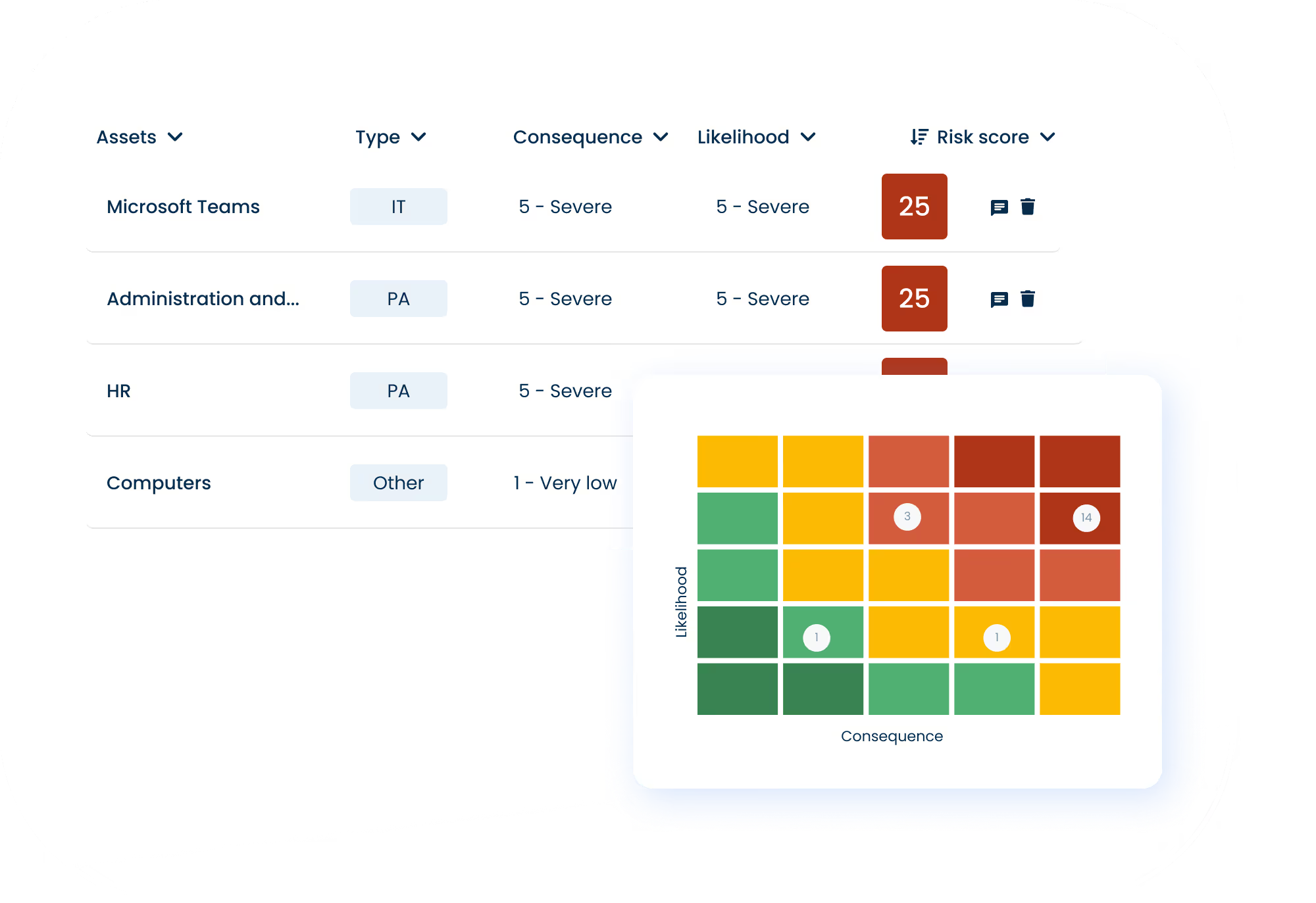
Risk assess your ICT providers
Lay the foundation for long-term resilience with a guided, transparent approach to ICT risk management.
Assign responsibilities by linking owners and approvers to each risk.
Maintain a full risk register with version history, exports, and audit logs.
Identify, score, and mitigate risks using a guided framework.
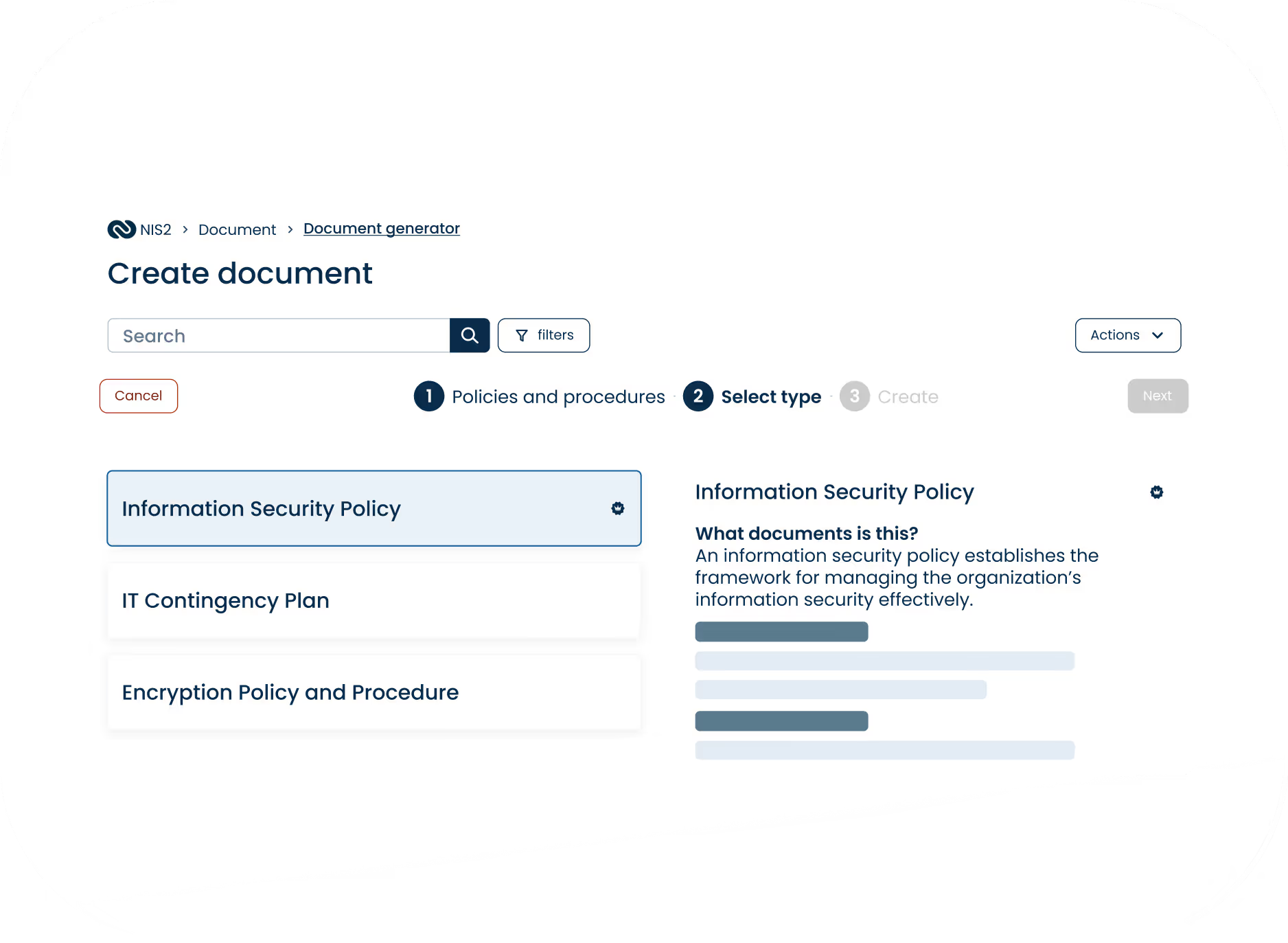
Create audit-ready documents
Generate the documents you need to comply with DORA.
Create compliant security documentation through guided questionnaires.
Stay up to date with automated reminders and version tracking for every document.
Build a public-facing Trust Center to showcase your DORA compliance.
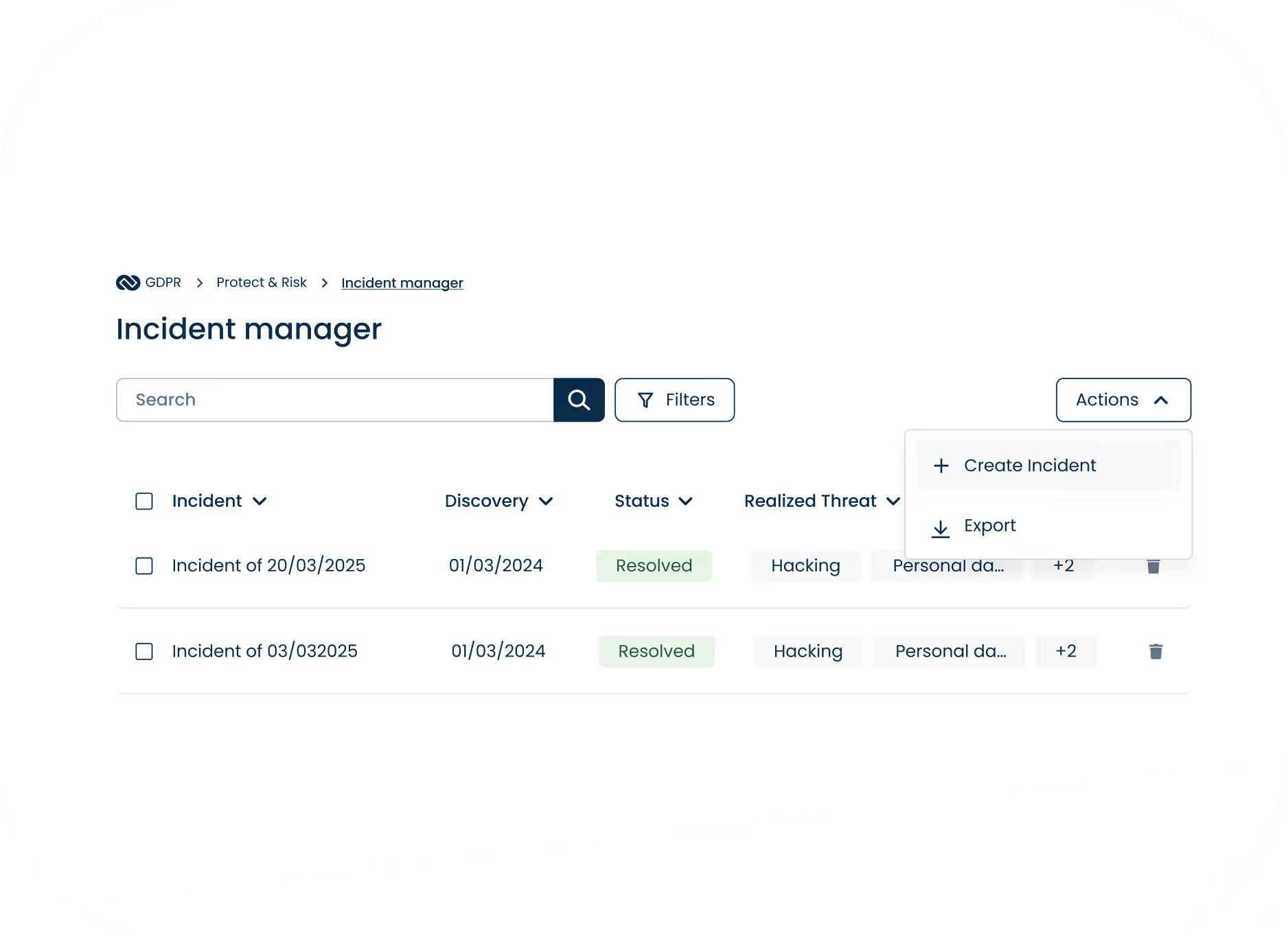
Report and document incidents
Stay prepared for regulatory inspections by logging and monitoring incidents.
Register incidents with severity, impact, and timestamps.
Document actions taken, outcomes, and root-cause analysis.
Maintain a complete, exportable incident log for internal use or regulatory review.
Ready to take control of your DORA compliance?
We’ll help you turn complex requirements into clear, manageable actions. From legal expertise to automation, everything you need is built into one platform.
Frequently asked questions
The NIS1 directive was introduced as the EU’s initial cybersecurity legislation to enhance the ability of network and information systems to withstand cyber risks. However, the COVID-19 pandemic has expanded the range of threats, necessitating the development of new measures.
The European Commission recognized certain shortcomings in the existing NIS1, including:
- Inconsistent resilience levels across Member States and sectors
- A lack of shared understanding regarding threats
- Inadequate joint crisis response capabilities
- Insufficient cyber resilience among EU businesses
Consequently, in December 2020, the Commission put forth new regulations aimed at reinforcing cyber resilience within the EU, which were subsequently adopted in November 2022.
The NIS2 is a directive which means that it will have to be implemented with national legislation. The member states in the EU must do so before 18 October 2024.
The NIS2 directive covers entities from the following sectors:
Essential sectors:
- Energy (electricity, oil, gas, district heating and cooling, and hydrogen).
- Transport (air, rail, water and road)
- Healthcare
- Water supply (drinking water, wastewater).
- Digital infrastructure (telecom, DNS, TLD, cloud service, data centres, trust service providers).
- Finance (banking, financial market infrastructure)
- Public administration
- Space
Important sectors:
- Digital providers (online markets, search engines, social networks)
- Postal services
- Waste management
- Foods
- Manufacturing (medical devices, electronics, machinery, transport equipment)
- Chemicals (production and distrubition)
- Research
While both essential and important sectors are required to adhere to the same security measures, there is a difference in the level of supervision. Entities classified as “essential” are subject to proactive supervision, meaning they are monitored regularly to ensure compliance. On the other hand, “important” entities are monitored only in response to reported incidents of non-compliance.
This differentiation aims to prioritize the continuous operation and resilience of critical services while still ensuring that all entities maintain the necessary security measures to protect against cyber threats.
The NIS2 establishes a comprehensive framework for supervisory and enforcement activities across Member States. Competent authorities are responsible for overseeing essential and important entities’ compliance with the regulations. Supervisory measures include audits, checks, information requests, and access to documents.
The directive introduces a consistent framework for sanctions, including binding instructions, implementation of security audit recommendations, alignment with NIS requirements, and administrative fines. Administrative fines vary based on entity classification, with essential entities facing fines up to €10,000,000 or 2% of annual turnover, and important entities facing fines up to €7,000,000 or 1.4% of annual turnover. Supervisory authorities must consider the nature and severity of the breach and any damages or losses incurred when exercising enforcement powers.
Opposite to the GDPR, the NIS2 also holds natural persons in senior management positions within covered entities accountable.
The NIS2 focuses on improving cyber risk management through clear responsibilities, effective planning, and enhanced cooperation within the EU.
To achieve this, NIS2 mandates Member States to designate national authorities responsible for cyber crisis management. It also introduces the requirement for national large-scale cybersecurity incident and crisis response plans. Additionally, NIS2 establishes the European cyber crisis liaison organization network (EU-CYCLONe). This network plays a vital role in the EU’s cyber crisis management framework, facilitating coordinated responses to significant cybersecurity incidents and crises. The combination of designated authorities, national response plans, and the EU-CYCLONe network ensures a more coordinated and efficient approach to managing large-scale cybersecurity incidents and crises across the European Union.
NIS2 will strengthen and streamline cybersecurity requirements for covered entities by requiring all companies to address a core set of 10 minimum requirements in their cybersecurity risk management policies.
These elements include incident handling, supply chain security, vulnerability handling and disclosure, and the use of cryptography. The NIS2 also includes a multiple-stage approach to incident reporting, which strikes a balance between swift reporting to prevent the spread of incidents and in-depth reporting to draw valuable lessons learned.
Affected companies have 24 hours to submit an early warning, 72 hours to submit an incident notification, and one month to submit a final report. This will help to reduce the additional burden for companies operating in multiple member states and ensure that all companies are addressing the necessary cybersecurity requirements.
Automating NIS2 compliance can help streamline and simplify the process for covered entities. ComplyCloud are currently developing a powerful tool to do exactly this.
Below, we have listed areas where we see a major potential in helping you automating and streamlining your NIS2 compliance:
- Annual wheel of work: An annual wheel of work regularly giving you tasks will make sure you don’t miss anything in your ongoing work and give you peace of mind.
- Risk assessment and management: Automated methods to conduct regular risk assessments, identify vulnerabilities, and prioritize mitigation efforts.
- Incident management: A simple and intuitive incident management system can help you getting managing incidents in a smooth and compliant wat.
- Documentation: Dynamic questionnaires can make you capable of creating any necessary document much faster and with a higher quality than if you had to create them from scratch.
- Employee training and awareness: Carrying out awareness training ensuring that your employees are knowledgeable about their roles and responsibilities under NIS2 will be key to strengthen your organization’s security against cyber-attacks.
- Gap-analyses: Gap-analyses will guide you through the requirements and make you aware of any gaps you might have.
- Vendor management: A system for vendor management will help you comply with the requirements to supply chain security.
